
Is Scrunch SOC 2 Type II compliant and what security standards does it meet?
- Also asked as:
- Does Scrunch have SOC 2 certification?
- Is Scrunch data secure and compliant?
Yes, Scrunch has successfully completed a SOC 2 Type II audit conducted by an independent third-party auditor.
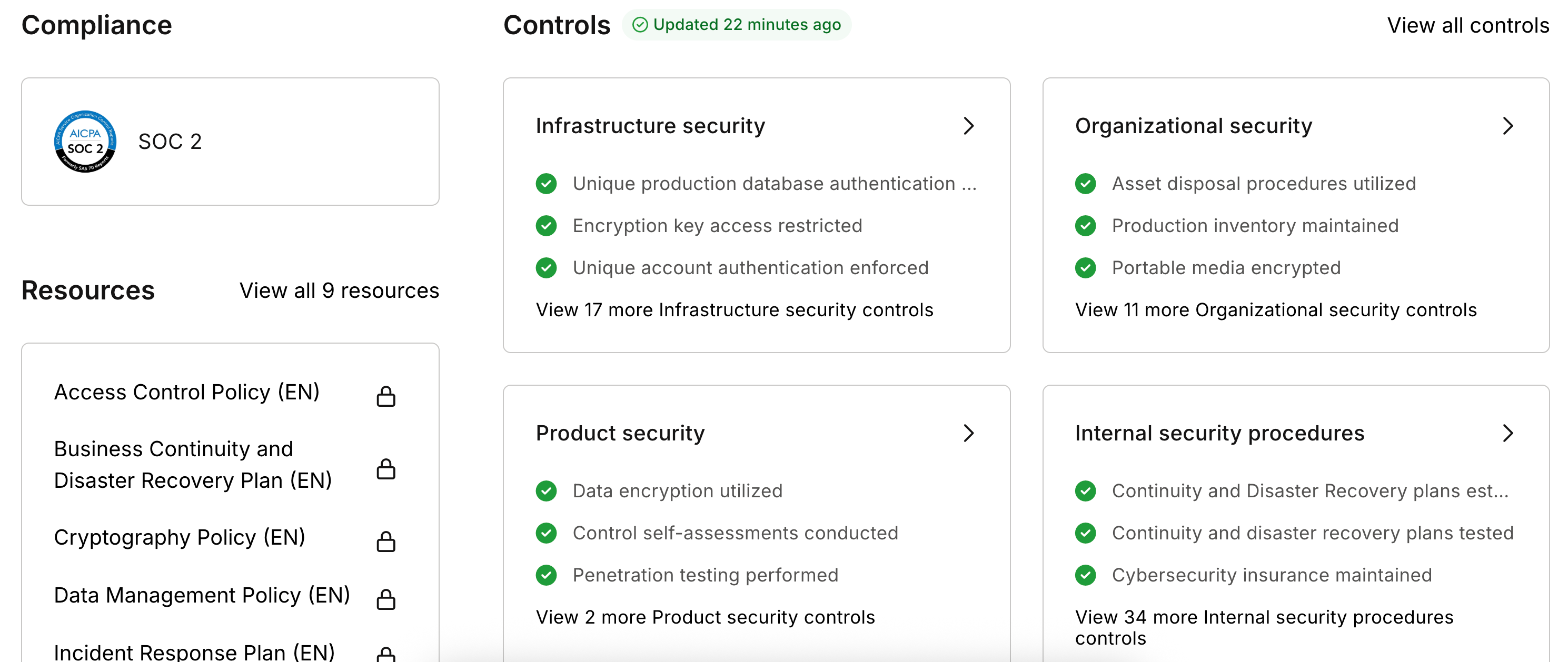
Additional context: Scrunch maintains comprehensive security controls covering infrastructure security, organizational security, product security, internal security procedures, and data privacy protections.
Example
For example, users can independently verify Scrunch's security posture through the Scrunch Trust Center, which provides:
- Current SOC 2 Type II audit reports and certification status
- Detailed security and data handling policies
- Information about data collection methodologies
- Complete list of third-party subprocessors
The Trust Center is publicly accessible without requiring a Scrunch account.
Follow-up question: What enterprise security features does Scrunch provide?
Beyond SOC 2 Type II compliance, Scrunch implements enterprise-grade security features like:
Identity and access management
Scrunch provides options for SAML and OAuth-based single sign-on (SSO) to enable centralized access control. Role-based access control (RBAC) provides granular team permissions without security compromises.
Regulatory compliance
Scrunch is compliant with GDPR for EU data protection and CCPA for California residents’ privacy rights. Scrunch does not sell personal information under any circumstances.
Other enterprise features
Scrunch offers comprehensive audit logs to track all user actions, detailed analytics dashboards, enterprise support with guaranteed SLAs, and secure API integrations with token-based authentication.
Related FAQs
What user roles and permissions are available in Scrunch?
Four user roles are available in Scrunch: Admin, Editor, Viewer, and Guest. Admins have full organizational access, Editors can create and modify content, Viewers have read-only access, and Guests (agency accounts only) see only specific brands. Permissions can be customized per brand for granular control.
What single sign-on (SSO) providers does Scrunch support?
The Scrunch Enterprise plan supports single sign-on (SSO) with major identity providers, including Okta, Microsoft Entra ID (formerly Azure AD), and Google Workspace. Any SAML 2.0 or OIDC-compliant identity provider is also supported.
Does Scrunch collect personal information from people using AI platforms like ChatGPT?
No, Scrunch doesn’t collect personal information from members of the general public as part of its service offerings.